With landmark laws such as the DPDPA, GDPR, CCPA and every other law across the globe; one term is common, undisputed and has become central in compliance conversations: “data deletion.” Under these regimes, organizations may be required to delete personal data upon request by the data principal (the individual) or when the data is no longer necessary for the purpose for which it was collected.
The Hard Truth: Deletion Is Often a Myth
In practice, however, true deletion is more myth than fact. What organisations quite commonly achieve is logical deletion, removing a record or dropping a pointer while the underlying data footprint remains. For example:
- Data may still reside in memory caches, logs, active databases, replication/archival systems, cloud object‐storage versions or snapshots.
- Physical blocks or sectors on HDDs or SSDs may remain intact, rendering the data technically recoverable.
- It might exist in redundant backups or disaster-recovery replicas, where deletion is operationally risky or not feasible.
From a forensic standpoint, unless the storage medium has been overwritten or destroyed, the data could be reconstructed. This leads to the uncomfortable but increasingly recognized reality: data deletion as users think of it rarely happens at the physical level.
The Reality: Data Purging (or Sanitization)
What organizations can achieve is data purging or media sanitization, which involves irreversible removal of data across all systems including backup and archival layers, and often physical sanitization or destruction of the storage medium. Key techniques include:
- Overwriting blocks or sectors with specified patterns (e.g., zeroes, ones, random data).
- Cryptographic shredding: encrypt the data and destroy the encryption key, rendering the data irrecoverable.
- Physical destruction: shredding, degaussing, incineration of the media in extreme scenarios.
Purging is more operationally intensive, often expensive and logistically complex — especially in environments with long retention requirements (such as regulated sectors like banking, insurance and telecoms).
The Compliance Paradox
Here lies a core tension: regulations say delete, but business/sectoral rules often say retain. For instance, a bank might have KYC or audit-trail obligations that require data retention for a decade or more, yet a user may request deletion under privacy law. The result: organizations may perform logical deletion (removing usability) but retain data in a sanitized form, or provide cryptographic deletion as practical compromise.
Acceptable Technical Approaches and Standards
To bridge legislative intent and operational capability, organizations should design deletion/sanitization programs grounded in recognized standards. Key standards include:
- DoD 5220.22‑M: Early U.S. Department of Defense guideline involving multiple overwrite passes (e.g., 3-pass: zeros, ones, random).
- NIST SP 800‑88 (Guidelines for Media Sanitization): A modern, broadly referenced U.S. standard covering “clear”, “purge” and “destroy” approaches depending on media type and sensitivity.
- IEEE 2883: A newer standard addressing sanitization in modern storage (SSD, flash, etc.).
- Other standards: e.g., UK’s IS5 (Infosec Standard 5) for media sanitization.
Organizations should adopt a data lifecycle policy where deletion (or purging) is triggered by retention expiry, user request (subject to legal hold), or when data is no longer needed. Audit trails, certificates of erasure and verifiable logs form part of a defensible posture.
If your data can be recovered, was it ever really deleted? This is the honest question organisations must ask. Let’s open the conversation:
- Should one-way encryption (key destruction) be formally accepted as “deletion” under law?
- How can organisations respect user deletion requests when sectoral rules require retention?
- Are we due for sector-specific rules under frameworks like the upcoming Digital Personal Data Protection Act, 2023 (DPDPA) in India to clarify this contradiction?
Solution in Practice
To operationalize secure erasure/purging, enterprises can deploy specialized tools and services. For example:
- Concur – Consent Manager: Offers certified data erasure software (software-based overwriting and remote management) for HDDs, SSDs, storage arrays etc. Supports many standards (DoD, NIST, IEEE) and provides audit-ready certificates for many of offerings.
- Other asset-disposition / sanitization providers (though not named here) also offer hardware and software solutions for end-of-life media disposal and data sanitization across hybrid/cloud environments.
Practical Recommendations for Organizations
- Define retention vs. deletion policy: Map out data categories plus legal/regulatory retention obligations, then tie in user-request deletion logic.
- Build sanitization workflows: Determine whether overwriting, cryptographic deletion or destruction is appropriate per media type and sensitivity.
- Automate reporting and certification: Use tools that issue tamper-proof certificates of erasure, maintain logs of when and how data was purged.
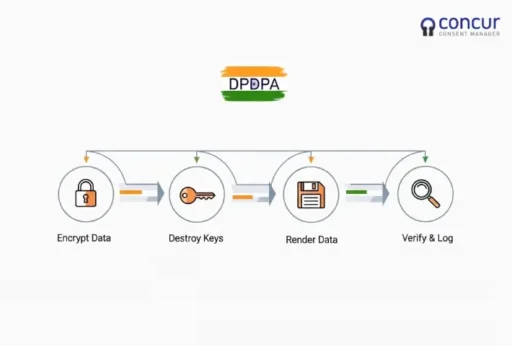
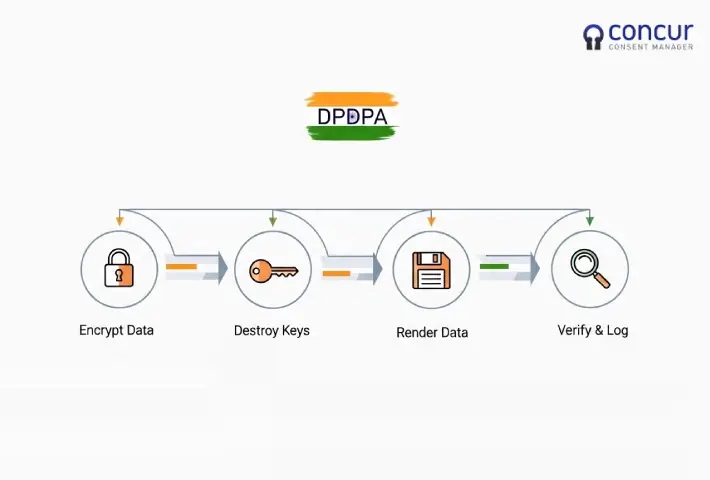
- Use cryptographic deletion when full purging is infeasible: If retention obligations exist, encrypt the data and destroy keys; this renders it unusable while preserving records.
- Educate stakeholders: Privacy officers, boards and technologists must understand the difference between “logical deletion” and “purging” — this avoids mismatched expectations with users and regulators.
- Engage vendors/solutions early: If you rely on cloud, backup or third-party processors, ensure your purge requirements extend into their environments.
- Plan for modern media: SSDs, cloud object stores, virtual machines have different sanitization properties—apply standards like NIST SP 800-88 or IEEE 2883 rather than legacy HDD approaches.
In the real world of corporate data privacy, “deletion” as users expect it seldom exists — what occurs instead is logical removal while the underlying footprint remains somewhere. To bridge perception and practice, organizations must embrace purging, sanitization and demonstrable audit-proof destruction. Only then can they genuinely claim they’ve erased the data.